Are you doing enough to improve Infor M3 user security? A high level of cybersecurity is crucial now, as attacks by bad actors are increasing. There were more than 37 billion breached records in 2020—a growth of 141% from 2019.
Your business needs a modernized security strategy to protect your users, data, and IT resources. With a greater focus on user authentication and authorization, you can eliminate security vulnerabilities in your business.
Read on to learn more about how you can use Infor M3 user security to safeguard your mission-critical IT deployments from user threats.
What’s the Difference Between Authentication and Authorization?
Let’s start by defining what security authentication and authorization are and how the two primary processes of user security occupy different roles in your security strategy.
Authentication
Security authentication is a first defense protocol that validates the identity of a user and confirms they are who they claim to be.
As a software solution, the authentication process compares the user’s credentials against a system file when they log in, granting, or rejecting the user access if it finds a match.
For example, passwords are a traditional and well-known authentication method. Users can also validate their identities using new technology options such as biometrics (fingerprint or eye scan), authentication management company apps such as Okta, or one-time pins (OTP). The more authenticators you have, the harder it is for a security breach.
The authentication process is visible to the user, but all input data remains anonymous through ID tokens.
Authorization
Security authorization provides the second line of defense after an authenticated user gains access to your IT infrastructure. It determines a user’s permissions inside your business platform, ensuring that people can access the information, files, or resources within their clearance levels.
Authorization solutions work in the background through settings maintained by the security team, helping keep users in their correct place. It ensures users never overstep their boundaries or snoop on sensitive files. If a user’s credentials are compromised, the bad actor cannot access data blocked by the rules laid about by your authorization process.
Unlike authentication, authorization is not visible to users, and data moves through access tokens rather than ID tokens.
How Infor M3 Provides Authentication User Security
Infor M3 helps organizations plan, prepare, and protect against data breaches by facilitating and managing user verification and access permissions.
The primary authentication product, Infor Federated Services (IFS), streamlines IT security by allowing for a single login that can switch between multiple applications, helping reduce user friction.
As a critical Infor Cloudsuite tool, IFS centralizes user role management around a suite of applications, enabling you to add users, reset passwords, and delete roles in a single, easy-to-use Infor system. You can see the security roles available in IFS below.

Use An Identity Provider For Integrations
IFS also lets you support seamless integrations with existing Identity Providers (IDPs), connecting to any application in a few mouse clicks—without exposing your business to risks. Most users of Infor Cloudsuite have an existing Identity Provider, and IFS can help with integration.
For example, third-party authenticators like Okta and One-Login enable authentication and provisioning capabilities that streamline access management across all your apps.
The Importance of Security Token Services (STSs)
Heterogeneous environments often require web services to authenticate service clients and control their access. These web services depend on STSs to issue signed tokens.
As an authentication broker, STSs provide a standard access control infrastructure for a group of applications, enabling Single Sign-on (SSO) in multi-company networks. Tokens act as a timed key for users entering into web environments, making access an improved and secure experience.
Infor’s built-in Security Token Services allows you to manage security tokens as needed. You can validate, issue, and renew token claims to permitted users with better efficiency.
How Infor M3 Provides Authorization User Security
Infor M3 also offers several software solutions for authorization security, enabling employees to access the correct data without compromising security.
Infor M3 Roles
Infor M3 Business Engine’s authorization by roles allows businesses to control access to critical data based on specific functions. You take on undue risk by allowing your workforce undesignated access to your data pool. Besides being vulnerable to sabotage and malicious activity, excessive user access across the entire system reduces your system’s total security.
The role-based authorization of Infor M3 Business Engine defines the programs, or program features a user can access, allowing them to work only with the resources they need to remain productive. By assigning roles to Infor M3 users, you can simplify the management of large teams and improve Infor M3 user security. The roles that can be assigned in M3 are showcased in the following image.
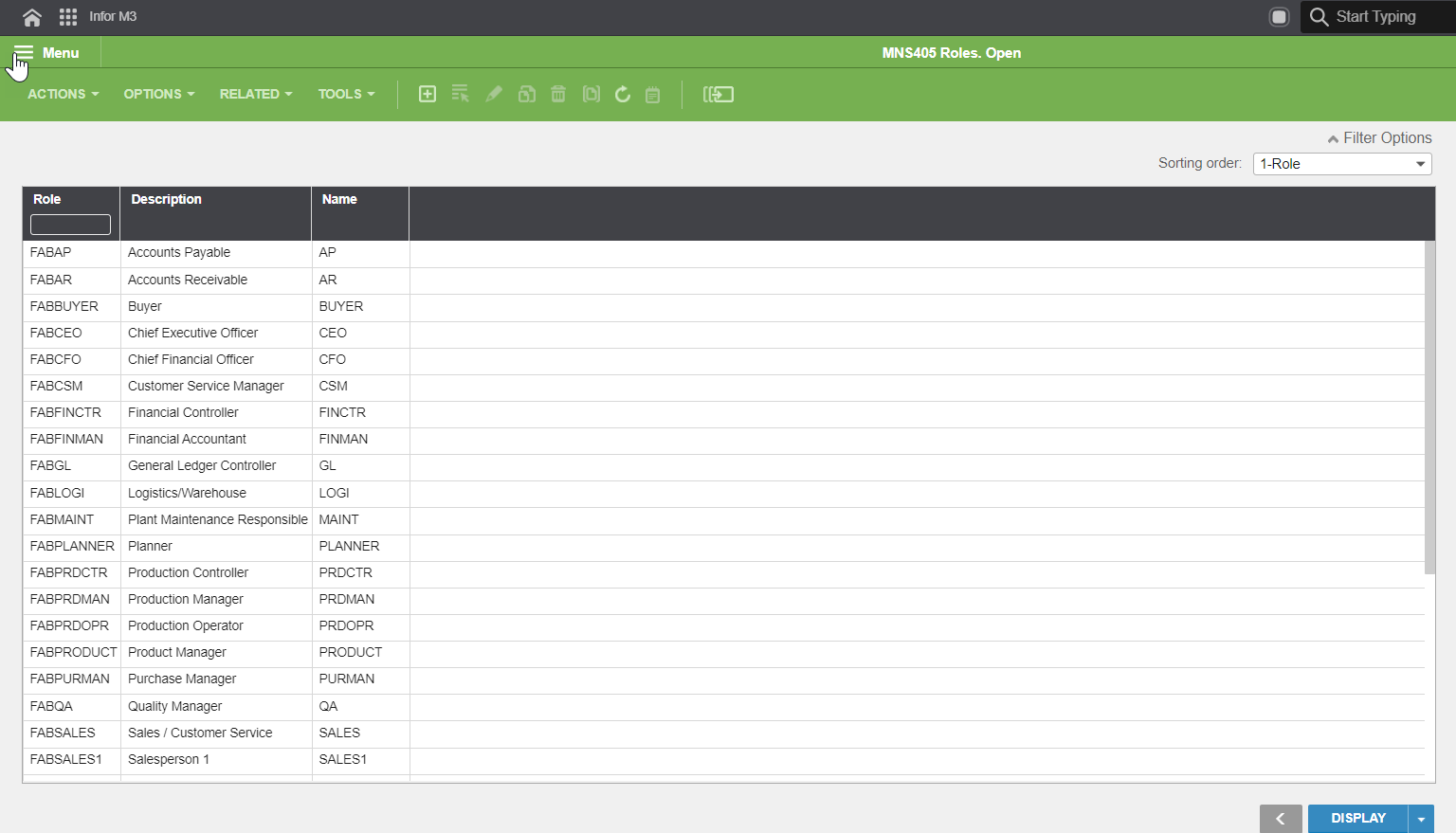
User Dataset Access
With Infor M3 User Dataset Access, you can improve user security in your enterprise by restricting access based on datasets such as gender or age. You can create categories that store users’ metadata, facilitating further access control to systems based on specific user conditions, leading to granular authorization requirements.
User Management Rights
Infor’s has a security feature for user rights management, which lets you control user access to tasks that are often restricted to superusers, dividing their privileges among several administrators.
Besides giving all levels of management the time and resources to focus on other business-critical operations, user rights management offers several additional benefits:
- Efficient Records: Keep a record of all users and how they received their privileges.
- Audit Mapping: Maintain an audit trail of all files, identifying user access and access type.
- Restriction Management: Track employees with legitimate needs for open restrictions and remove those who no longer deserve access.
Due diligence towards user rights promotes better security among employees and can help you track bad actors who wrongfully enter your systems.
IDO Elements and Attributes
An Intelligent Data Object (IDO) encapsulates units of information and logic called from the client layer to interact with data in the database.
It implements methods and properties that let clients load and update data collections or retrieve information about data.
Infor M3 embedded verification and security protocols sit between the user’s machine and the database server to protect data privacy as it transits the system, further improving user security.
Wrap Up
Malicious actors can compromise even the most secure infrastructure, and they often exploit weak points in user management to gain access.
You need a comprehensive user security strategy as attacks increase, and the solutions Infor M3 offers can help you manage authorization and authentication deployments.
If you struggle with security implementation, Doppio Group can help you strengthen your security posture to protect your data and users and also drive more value from your IT systems.
If you want to learn how to improve Infor M3 user security, get in touch by filling out our contact form.





